How Fraudsters Are Using Synthetic Identities
Pathways to Synthetic Identity Fraud
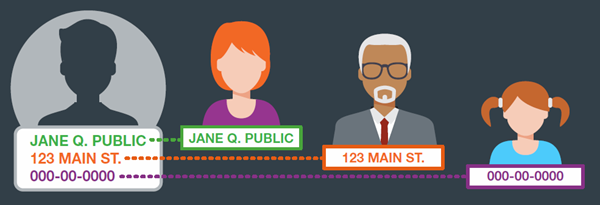
Fabricated social security numbers (SSNs) and authorized user abuse are the two main pathways into synthetic identity fraud. Fraudsters can build synthetic identities by creating a fake SSN or obtaining/stealing a real SSN and adding non-matching identifying information such as name, date of birth, and address.
Perpetrators often prefer to steal randomized SSNs or purchase them from hackers who breach public or private databases that contain personally identifiable information. Then the fraudster uses the synthetic identity to apply for a line of credit, typically at a bank. The bank submits an inquiry to credit bureaus about the applicant’s credit history. The credit bureaus initially report that an associated profile does not exist and the bank may reject the application; however, the credit inquiry generates a credit profile for the synthetic identity in the credit bureaus’ databases.
At this stage, the perpetrator will typically apply for multiple credit cards and other products marketed to consumers who are new to credit. They maintain good credit over time to build up credit limits and apply for more cards.
Most times, the fraudster ends up charging the maximum amount on credit cards and not paying the bill (known as “bust-out” fraud) or they may launder the money between multiple accounts. An authorized user is someone who is granted access to another person’s credit card account. Authorized users receive full access to the account’s credit line but are not legally responsible for paying the balance or associated fees that result from their use of the account. Once an authorized user is added to a credit card account, the issuer will begin relaying account information to the major credit bureaus on a monthly basis under the authorized user’s name. As long as the account is managed well, the authorized user’s credit report should reflect positive information, whereas account mismanagement (e.g., missing payments or exceeding the credit limit) produces the opposite effect.
If the authorized user has no previous credit history, his or her first credit score should be generated within six months. Most major credit-card companies report authorized users’ account information to the major credit bureaus each month. Assuming the information reflects responsible use, this process will help to improve the authorized user’s credit standing, perhaps elevating it all the way to the “excellent” range over time. While the practice of adding authorized users may not be illegal, it can pose significant risks to financial institutions – leading to authorized user abuse.
Sometimes called credit boosting or piggybacking, authorized user abuse occurs when low-risk primary card owners “rent” their tradelines with extensive credit histories, high credit limits and solid repayment profiles to others – most times, knowingly, to fraudsters. The synthetic scheme looks very similar to the appropriate use, and requires three ingredients:
- A primary credit card owner – Who is in good standing, with a high credit score, pays consistently and looks like a good credit card customer
- The fraudster – Who wants to create a synthetic identity and needs to get a credit file and good credit score matched to it
- Agreement/Collusion – The fraudster pays the primary card owner to add him as an authorized user to the account, usually for a certain time limit, after which the fraudster is dropped/terminated from the primary account and attempts to gain lines of credits with the new credit report
Fraud Identification
At the 2017 US Government Accountability Office (GAO) Forum1, panelists said that credit bureaus and data brokers were often positioned to have the best information overall on possible synthetic identity fraud because they have data from a cross-section of accounts and financial institutions. The most useful application of this data involves returning both positive confirmations of an SSN match and several negative alerts that can signal the creation of a synthetic identity or other SSN-related fraud at account opening — before any damage is done.
How Equifax Can Help
FraudIQ®
Synthetic ID Alerts, delivered in batch or real-time, are based
on patent-pending algorithms that analyze attributes such as
authorized user velocity and identity discrepancies to help determine
if the identity presented is potentially synthetic. When you submit a
batch file or real-time inquiry and suspicious information is found,
the synthetic ID alert will be returned, providing you with the
information your business needs to assess in order to detect this type
of fraud. Successfully protecting your business against fraud requires
a multi-layered approach. FraudIQ Synthetic ID Alerts are part of an
integrated
suite of identity verification, authentication and fraud detection
solutions that leverage Equifax’s proprietary and differentiated
data. This data helps you assess modeling behavior, rather than just
data checking – which can provide a better output for
prevention. 
By Cathleen Donahoo Director, Product Management Equifax Identity & Fraud Solutions
1 GAO “Highlights of a Forum: Combating Synthetic Identity Fraud,” July 2017
Recommended for you